Fortify Your Business with
Way2Protect's Ultimate Cybersecurity Shield
Transform cybersecurity from a challenge into your competitive advantage.
Fortify Your Business with Way2Protect's Ultimate Cybersecurity Shield
Transform cybersecurity from a challenge into your competitive advantage.
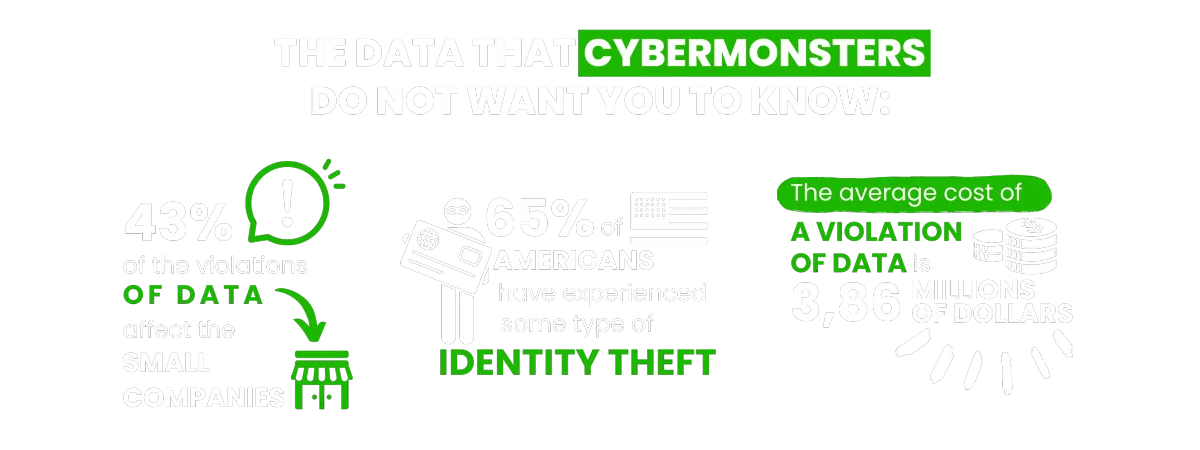
You find these and other figures in my book Happily Ever Cyber and on Cisa.gov

Find out how to push Cybermonsters away from your private data
With tips to help prevent a cyber attack protecting your family, work environment and yourself:
AS SEEN ON:


Find out how to push Cybermonsters away from your private data
With tips to help prevent a cyber attack protecting your family, work environment and yourself:
AS SEEN ON:

Push Cybermonsters away from your private data.
Subscribe to my newsletter about cybersecurity and cyber safety. New issues every Tuesday.

Push Cybermonsters away from your private data.
Subscribe to my newsletter about cybersecurity and cyber safety. New issues every Tuesday.

Protect those that matters most to you:

Family
Protect your child(ren), teens,
and your parents.

Business Owners
Protect your data, your customer's information, your employees,
and your brand!

Yourself
Have peace of mind online!
International Bestselling & Award-Winning Cyber Safety Author
Identity theft & cyber crime can happen to anyone.




Why choosing us?
In a world full of digital distractions, we understand the importance of cultivating a healthy balance. At Way2Protect, our mission is clear: to be your trusted guide to a conscious and protected online experience, both for you and for what you value most: your family, your business, and your peace of mind.
Way2Protect becomes your fundamental ally in your digital world, providing you with hassle-free security and adapting cybersecurity practices to your routine without sacrificing your time. We facilitate the process, guiding you in the implementation of effective cybersecurity practices to protect your family, your business, and your work teams.
Why choosing us?
In a world full of digital distractions, we understand the importance of cultivating a healthy balance. At Way2Protect, our mission is clear: to be your trusted guide to a conscious and protected online experience, both for you and for what you value most: your family, your business, and your peace of mind.
Way2Protect becomes your fundamental ally in your digital world, providing you with hassle-free security and adapting cybersecurity practices to your routine without sacrificing your time. We facilitate the process, guiding you in the implementation of effective cybersecurity practices to protect your family, your business, and your work teams.

Get the latest news in the Cyber Security World

Digital Fortresses: Ancient Defensive Strategies in Modern Cybersecurity
In the shadowy realm of cybersecurity, where digital marauders prowl and data breaches loom like storm clouds on the horizon, we find ourselves in a constant battle to protect our virtual assets. As we forge ahead into an increasingly interconnected future, it's easy to forget that the principles of defense are as old as civilization itself. The fortresses and castles of antiquity, with their imposing walls and ingenious defensive mechanisms, hold surprising parallels to the cybersecurity strategies of today. This exploration will take us on a journey through time, drawing unexpected connections between ancient stonework and modern firewalls, revealing how the wisdom of the past continues to inform our digital present.
The Moat and the Firewall: Creating a Digital No Man's Land
Picture, if you will, a medieval castle surrounded by a deep, water-filled moat. This first line of defense served not only as a physical barrier but also as a psychological deterrent to would-be invaders. The moat created a clear demarcation between the outside world and the protected inner sanctum of the castle, forcing attackers to expose themselves as they attempted to cross.
In the digital realm, firewalls serve a strikingly similar purpose. Like moats, firewalls create a buffer zone between trusted internal networks and the untrusted outside world of the internet. They monitor and control incoming and outgoing network traffic based on predetermined security rules, effectively creating a digital no man's land that potential attackers must navigate.
Modern firewalls have evolved beyond simple packet filtering to include stateful inspection, application-layer filtering, and even AI-driven threat detection. These advanced features mirror the evolution of moats, which over time incorporated additional elements like drawbridges, portcullises, and murder holes to enhance their defensive capabilities.
The psychological aspect of the moat also finds its parallel in cybersecurity. A well-configured firewall sends a clear message to potential attackers: "This network is protected, and breaching it will not be easy." This deterrent effect can be as valuable as the technical protection itself, encouraging less determined attackers to seek easier targets elsewhere.
Watchtowers and Intrusion Detection Systems: Vigilant Sentinels
High above the castle walls, vigilant sentries manned watchtowers, scanning the horizon for signs of approaching danger. These elevated vantage points allowed defenders to spot threats early, providing crucial time to prepare defenses and mobilize forces. The watchmen's keen eyes and intimate knowledge of the surrounding landscape were often the difference between a successful defense and a catastrophic breach.
In our digital fortresses, Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) play the role of these tireless sentinels. These systems constantly monitor network traffic for suspicious activities, anomalies, or known attack signatures. Like the watchmen of old, IDS/IPS solutions provide early warning of potential threats, allowing security teams to respond swiftly and decisively.
Modern IDS/IPS systems have capabilities that would seem like sorcery to medieval watchmen. They can analyze vast amounts of data in real-time, use machine learning algorithms to detect novel threats, and even take autonomous actions to thwart attacks in progress. Yet, the core principle remains the same: vigilant observation and rapid response are key to effective defense.
The parallels extend further when we consider the importance of context and pattern recognition. Just as an experienced watchman could distinguish between a dust cloud raised by a merchant caravan and the approach of an enemy army, sophisticated IDS/IPS systems can differentiate between benign network anomalies and genuine threats. This ability to contextualize observations and make informed judgments is crucial in both ancient and modern defensive strategies.
Arrow Slits and Data Encryption: Protecting Assets While Maintaining Functionality
Castle designers faced a perennial challenge: how to allow defenders to attack enemies while minimizing their own vulnerability. The elegant solution came in the form of arrow slits – narrow openings in walls that allowed archers to fire upon attackers while remaining largely protected from return fire. These slits were carefully designed to provide maximum visibility and range of motion for the defender while presenting the smallest possible target to the enemy.
In the realm of cybersecurity, data encryption serves a remarkably similar function. Encryption allows data to be used and transmitted while keeping it secure from unauthorized access. Like an arrow slit, encryption provides a narrow, controlled channel through which data can be utilized without exposing it to broader threats.
Modern encryption algorithms, such as AES (Advanced Encryption Standard) and RSA, are the digital equivalent of intricately designed arrow slits. They allow legitimate users to access and utilize data while presenting an nearly insurmountable barrier to unauthorized parties. The mathematical complexity of these algorithms ensures that, like a well-designed arrow slit, the "opening" for legitimate use is precisely controlled and difficult for attackers to exploit.
The analogy extends to the concept of key management in cryptography. Just as castle defenders needed to carefully control access to arrow slits to prevent their use by infiltrators, modern organizations must meticulously manage encryption keys to ensure that only authorized parties can decrypt sensitive information. The principle of minimizing exposure while maintaining functionality remains constant across the centuries.

Concentric Walls and Defense in Depth: Layered Protection Strategies
The most formidable castles didn't rely on a single, impregnable wall. Instead, they employed a system of concentric defenses – multiple layers of walls, each designed to slow down and wear out attackers. This strategy, known as defense in depth, ensured that even if the outer wall was breached, invaders would face successive challenges before reaching the inner keep.
In modern cybersecurity, the principle of defense in depth is just as crucial. No single security measure, no matter how robust, can provide complete protection against the myriad of cyber threats. Instead, organizations implement multiple layers of security controls to create a comprehensive defensive posture.
These layers might include:
Perimeter defenses (firewalls, intrusion prevention systems)
Network segmentation
Access controls and authentication mechanisms
Endpoint protection
Data encryption
Regular security updates and patch management
Employee training and awareness programs
Each of these layers serves a specific purpose, much like the various defensive elements in a castle. The outer firewall might repel casual attacks, just as the outer wall of a castle deterred minor raiding parties. Network segmentation creates internal barriers, similar to the division of a castle into distinct wards. Strong authentication acts like the castle's gatehouse, controlling who gains entry to sensitive areas.
The strength of this approach lies in its redundancy and complementary nature. If one layer is compromised, the others continue to provide protection, buying time for detection and response. This echoes the way castle defenders could fall back to inner walls and keeps, continuously resisting even as outer defenses were overcome.

Secret Passages and Secure Tunnels: Protecting Critical Communications
Many castles incorporated hidden passages and escape tunnels, providing secure routes for communication, resupply, or evacuation in times of siege. These covert pathways allowed defenders to move resources and information without exposure to enemy observation or interference.
In the digital world, Virtual Private Networks (VPNs) and secure communication protocols serve a similar function. These technologies create encrypted "tunnels" through the public internet, allowing sensitive data to be transmitted securely between remote locations or users.
Like the secret passages of old, VPNs and secure protocols ensure that critical communications remain confidential and intact, even when passing through potentially hostile territory. They protect against eavesdropping, data tampering, and man-in-the-middle attacks, much as a well-hidden castle passage protected messengers from enemy archers and spies.
The parallel extends to the concept of "security through obscurity." Just as the effectiveness of a secret passage depended partly on its remaining secret, some aspects of network security rely on keeping certain details hidden from potential attackers. While this should never be the primary defense mechanism, the principle of not broadcasting unnecessary information about network architecture or security measures has its roots in these ancient practices.
Conclusion: Timeless Principles in a Digital Age
As we've journeyed through the stone halls of ancient fortresses and the silicon pathways of modern networks, a profound truth emerges: the fundamental principles of defense transcend time and technology. The need for layered protection, early warning systems, controlled access, and secure communication channels remains as relevant in our digital age as it was in the era of catapults and siege towers.
This exploration reveals more than just interesting parallels; it underscores the timeless nature of security challenges and the enduring value of strategic thinking in defense. By understanding these connections, we gain a deeper appreciation for the foundations of modern cybersecurity and perhaps gain new insights into addressing contemporary challenges.
As we continue to build and refine our digital fortresses, let us not forget the lessons written in stone by our ancestors. The wisdom of the past, combined with the technology of the present, offers our best hope for securing the future.
Key Takeaways:
Firewalls, like moats, create crucial buffer zones between trusted and untrusted environments.
Intrusion Detection Systems serve as vigilant digital sentinels, much like castle watchtowers.
Data encryption, akin to arrow slits, allows for functionality while minimizing vulnerability.
Defense in depth strategies, employing multiple layers of security, mirror the concentric defenses of medieval castles.
Secure communication channels in cybersecurity parallel the secret passages of ancient fortifications.
Call to Action: Fortify Your Digital Castle
As guardians of digital assets in this modern age, it's imperative that we apply these timeless defensive principles to our cybersecurity strategies. Begin by assessing your current defenses through the lens of these historical parallels. Are your firewalls as formidable as a castle moat? Do you have vigilant "watchmen" monitoring for threats? Have you implemented multiple layers of defense to wear down potential attackers?
Take action today to reinforce your digital fortress. Implement robust firewall solutions, deploy advanced intrusion detection systems, and ensure your sensitive data is protected with strong encryption. Remember, in the realm of cybersecurity, as in ancient warfare, a strong defense is often the best offense. By building your digital castle with the wisdom of the ages, you can create a formidable bastion against the cyber threats of today and tomorrow.
Live Happily Ever Cyber!

Sandra Estok
Subscribe for more ways to protect what matters most to you against hackers, scammers, and Cybermonsters™



