Fortify Your Business with
Way2Protect's Ultimate Cybersecurity Shield
Transform cybersecurity from a challenge into your competitive advantage.
Fortify Your Business with Way2Protect's Ultimate Cybersecurity Shield
Transform cybersecurity from a challenge into your competitive advantage.
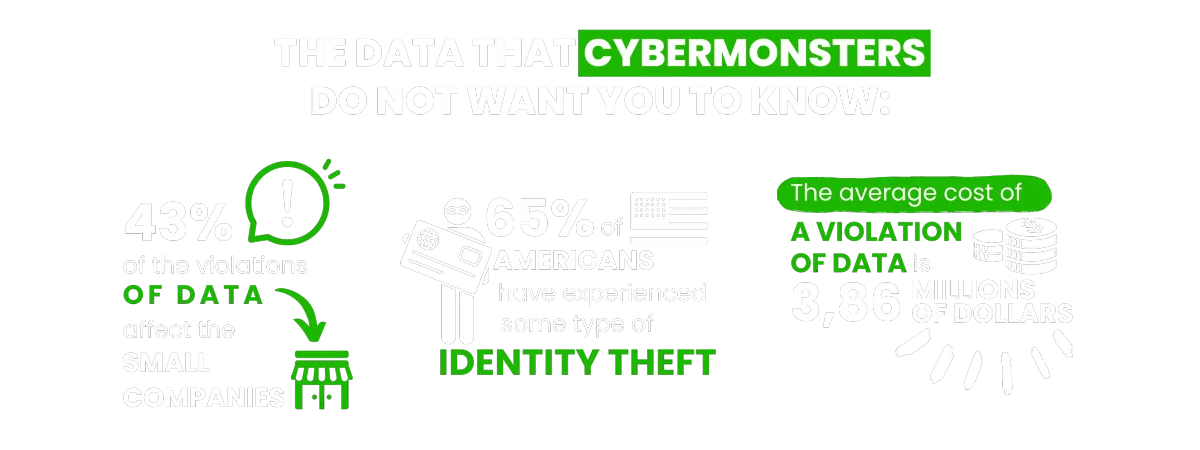
You find these and other figures in my book Happily Ever Cyber and on Cisa.gov

Find out how to push Cybermonsters away from your private data
With tips to help prevent a cyber attack protecting your family, work environment and yourself:
AS SEEN ON:


Find out how to push Cybermonsters away from your private data
With tips to help prevent a cyber attack protecting your family, work environment and yourself:
AS SEEN ON:

Push Cybermonsters away from your private data.
Subscribe to my newsletter about cybersecurity and cyber safety. New issues every Tuesday.

Push Cybermonsters away from your private data.
Subscribe to my newsletter about cybersecurity and cyber safety. New issues every Tuesday.

Protect those that matters most to you:

Family
Protect your child(ren), teens,
and your parents.

Business Owners
Protect your data, your customer's information, your employees,
and your brand!

Yourself
Have peace of mind online!
International Bestselling & Award-Winning Cyber Safety Author
Identity theft & cyber crime can happen to anyone.




Why choosing us?
In a world full of digital distractions, we understand the importance of cultivating a healthy balance. At Way2Protect, our mission is clear: to be your trusted guide to a conscious and protected online experience, both for you and for what you value most: your family, your business, and your peace of mind.
Way2Protect becomes your fundamental ally in your digital world, providing you with hassle-free security and adapting cybersecurity practices to your routine without sacrificing your time. We facilitate the process, guiding you in the implementation of effective cybersecurity practices to protect your family, your business, and your work teams.
Why choosing us?
In a world full of digital distractions, we understand the importance of cultivating a healthy balance. At Way2Protect, our mission is clear: to be your trusted guide to a conscious and protected online experience, both for you and for what you value most: your family, your business, and your peace of mind.
Way2Protect becomes your fundamental ally in your digital world, providing you with hassle-free security and adapting cybersecurity practices to your routine without sacrificing your time. We facilitate the process, guiding you in the implementation of effective cybersecurity practices to protect your family, your business, and your work teams.

Get the latest news in the Cyber Security World

Cyber Self-Defense 101: Protecting Your Digital Identity in the Dark Web Era
In an age where our lives are increasingly intertwined with the digital realm, the concept of self-defense has evolved beyond physical safety to encompass the protection of our virtual selves. Welcome to the world of cyber self-defense, a critical skill set for navigating the treacherous waters of the internet, particularly in the face of dark web threats. This comprehensive guide will equip you with the knowledge and tools necessary to safeguard your digital identity, offering a deep dive into the shadowy corners of the internet and providing actionable strategies to fortify your online presence.
1. Introduction to Cyber Self-Defense
Cyber self-defense is not merely a set of technical skills; it's a mindset, a proactive approach to protecting one's digital footprint in an increasingly interconnected world. Just as we lock our doors and remain vigilant in physical spaces, we must adopt similar practices in our digital lives. The stakes are high: our personal information, financial data, and even our reputations are at risk in the virtual realm.
The need for cyber self-defense has never been more pressing. With the proliferation of smart devices, cloud services, and social media platforms, our digital footprints have expanded exponentially. Each interaction, transaction, and shared piece of information creates a digital trail that, if left unprotected, can be exploited by malicious actors. The dark web, a hidden part of the internet not indexed by traditional search engines, has become a breeding ground for cybercriminals looking to profit from stolen identities and sensitive information.
As we delve deeper into this guide, we'll explore the intricacies of the dark web, identify common threats, and provide you with a comprehensive toolkit for protecting your digital identity. By the end of this journey, you'll be equipped with the knowledge and skills to implement a robust cyber self-defense strategy, ensuring that your digital self remains as secure as your physical one.
2. Understanding the Dark Web
To effectively protect ourselves in the digital realm, we must first understand one of its most notorious sectors: the dark web. Often shrouded in mystery and misconception, the dark web is a part of the internet that exists beyond the reach of standard search engines and requires specialized software to access.
The dark web operates on overlay networks, often referred to as "darknets," with The Onion Router (Tor) being the most well-known. These networks use encryption and routing techniques to ensure anonymity for their users. While this anonymity can serve legitimate purposes, such as protecting whistleblowers or facilitating communication in oppressive regimes, it also provides a haven for illicit activities.
It's crucial to distinguish the dark web from the deep web, a term often used interchangeably but incorrectly. The deep web refers to any part of the internet not indexed by search engines, which includes innocuous content like password-protected email accounts or subscription-based services. The dark web, in contrast, is a small subset of the deep web intentionally hidden and inaccessible through standard web browsers.
The architecture of the dark web is designed to obfuscate user identities and locations. When accessing a dark web site, your request is routed through a series of volunteer-operated servers called nodes. Each node only knows the identity of the previous and next node in the chain, making it extremely difficult to trace the origin or destination of the data.
While the dark web hosts various content, including political forums and literary clubs, it has gained notoriety as a marketplace for illegal goods and services. Cryptocurrencies like Bitcoin are often used for transactions, adding another layer of anonymity to these exchanges. Understanding this ecosystem is crucial for comprehending the nature of the threats that emanate from this hidden corner of the internet.

3. Common Threats on the Dark Web
The dark web poses a multitude of threats to individuals and organizations alike. By understanding these dangers, we can better prepare ourselves to combat them. Here are some of the most prevalent threats originating from or facilitated by the dark web:
Identity Theft and Fraud
Perhaps the most pervasive threat is the theft and sale of personal information. Cybercriminals harvest data through various means, including data breaches, phishing attacks, and malware infections. This information is then sold on dark web marketplaces, where it can be used for financial fraud, opening fraudulent accounts, or even blackmail.
Ransomware and Malware
The dark web serves as a distribution platform for sophisticated malware and ransomware. Cybercriminals can purchase these tools, often with customer support included, to launch attacks against individuals and organizations. The anonymity of the dark web makes it challenging to trace these transactions back to their source.
Doxxing and Extortion
Doxxing, the practice of revealing someone's personal information online without their consent, is facilitated by the dark web. Malicious actors can compile comprehensive dossiers on individuals, which can be used for extortion or harassment.
Financial Scams
The dark web hosts numerous financial scams, from fake investment opportunities to Ponzi schemes. The anonymity provided by cryptocurrencies makes these scams particularly dangerous, as transactions are often irreversible.
Corporate Espionage
Sensitive corporate information, including trade secrets and strategic plans, can be found on the dark web. This information may be obtained through insider threats or hacking and can cause significant damage to businesses.
Human Trafficking and Exploitation
One of the most egregious threats facilitated by the dark web is human trafficking and exploitation. The anonymity of the dark web makes it a platform for coordinating these heinous activities.
Understanding these threats is the first step in developing a robust cyber self-defense strategy. In the following sections, we'll explore practical steps and tools to protect yourself from these dark web dangers.
4. 5 Practical Steps for Protecting Your Digital Identity
Protecting your digital identity in the age of the dark web requires a multi-faceted approach. Here are five practical steps you can take to fortify your online presence:
1. Implement Strong, Unique Passwords and Multi-Factor Authentication
The foundation of digital security lies in robust password practices. Create complex, unique passwords for each of your online accounts. A password manager can help you generate and store these securely. Additionally, enable multi-factor authentication (MFA) wherever possible. MFA adds an extra layer of security by requiring a second form of verification, such as a fingerprint or a code sent to your phone, in addition to your password.
2. Regular Security Audits and Updates
Conduct regular audits of your online accounts and digital footprint. Review your privacy settings on social media platforms, check for any suspicious activity on your financial accounts, and ensure all your software and applications are up-to-date. Cybercriminals often exploit known vulnerabilities in outdated software, so staying current with updates is crucial.
3. Encrypt Your Data and Communications
Encryption is a powerful tool in your cyber self-defense arsenal. Use a Virtual Private Network (VPN) when connecting to public Wi-Fi networks to encrypt your internet traffic. For sensitive communications, consider using end-to-end encrypted messaging apps. When storing important documents in the cloud, ensure they are encrypted before uploading.
4. Practice Safe Browsing and Email Habits
Be vigilant when browsing the internet and handling emails. Avoid clicking on suspicious links or downloading attachments from unknown sources. Use ad-blockers and anti-malware extensions in your browser to reduce the risk of drive-by downloads and malicious advertisements. When it comes to emails, be wary of phishing attempts and verify the sender's identity before responding to requests for sensitive information.
5. Limit Your Digital Footprint
Reduce the amount of personal information you share online. Be selective about the details you provide on social media and online forms. Regularly review and delete old accounts you no longer use. The less information available about you online, the harder it is for cybercriminals to compile a comprehensive profile for identity theft or other malicious purposes.
By implementing these practical steps, you significantly reduce your vulnerability to dark web threats. However, cyber self-defense is an ongoing process that requires constant vigilance and adaptation to new threats as they emerge.
5. Tools and Resources for Monitoring Dark Web Activity
While it's crucial to take preventive measures, it's equally important to stay informed about potential threats to your digital identity. Several tools and resources can help you monitor dark web activity and detect if your personal information has been compromised:
Dark Web Monitoring Services
Services like LifeLock, ID Shield, and Experian IdentityWorks scan the dark web for your personal information. They alert you if your data appears in known breaches or is being traded on dark web forums. While these services can't prevent your information from appearing on the dark web, they provide early warning, allowing you to take swift action to mitigate potential damage.
Have I Been Pwned
This free service, created by security researcher Troy Hunt, allows you to check if your email address has been involved in known data breaches. It's a valuable tool for quickly assessing if your accounts have been compromised.
Blockchain Analysis Tools
For those concerned about cryptocurrency-related threats, blockchain analysis tools like Chainalysis and CipherTrace can help track suspicious transactions and identify potential scams or money laundering activities.
Open Source Intelligence (OSINT) Tools
Tools like Maltego and Shodan can help you understand what information about you or your organization is publicly available. This knowledge can guide your efforts to reduce your digital footprint and identify potential vulnerabilities.
Threat Intelligence Platforms
For businesses and advanced users, threat intelligence platforms like IBM X-Force Exchange and AlienVault OTX provide comprehensive insights into emerging cyber threats, including those originating from the dark web.
While these tools are powerful allies in your cyber self-defense strategy, it's important to use them responsibly and in compliance with applicable laws and regulations. Remember, the goal is to protect yourself, not to engage in any illicit activities on the dark web itself.

6. Case Study: Identity Theft Prevention Success Story
To illustrate the effectiveness of a comprehensive cyber self-defense strategy, let's examine the case of Sarah, a marketing executive who successfully thwarted an attempt at identity theft orchestrated through the dark web.
Sarah had always been cautious about her online presence, but after attending a cybersecurity seminar, she decided to implement a more robust protection plan. She started by using a password manager to create unique, complex passwords for all her accounts and enabled multi-factor authentication wherever possible.
As part of her new strategy, Sarah subscribed to a dark web monitoring service. Three months later, she received an alert that her email address and an old password had been found in a data dump on a dark web forum. Thanks to her use of unique passwords, the compromised password was no longer in use for any of her accounts.
Acting swiftly, Sarah took the following steps:
She immediately changed the passwords for any accounts that might have used the compromised password in the past.
She reviewed her credit reports and placed a fraud alert with the major credit bureaus.
She enabled additional security features on her financial accounts, including real-time transaction alerts.
She conducted a thorough audit of her online accounts, closing any that were no longer necessary.
A week later, Sarah received a notification from her bank about a suspicious attempt to open a new credit card in her name. Because of the fraud alert she had placed, the application was flagged for additional verification. Sarah was able to confirm that she had not applied for the card, and the attempt was thwarted.
This incident reinforced the importance of Sarah's proactive approach. Had she not implemented her cyber self-defense strategy, the outcome could have been drastically different. The potential identity thief might have succeeded in opening fraudulent accounts, damaging Sarah's credit score and potentially leading to significant financial losses.
Sarah's case demonstrates that while we can't always prevent our information from being exposed, we can take steps to minimize the damage and respond effectively when threats arise. By staying vigilant, utilizing available tools, and acting quickly, Sarah was able to protect her digital identity from a potentially devastating attack.
7. Conclusion: Embracing the 'Be I AM' Framework for Ongoing Protection
As we conclude our exploration of cyber self-defense in the dark web era, it's clear that protecting our digital identities is not a one-time task but an ongoing commitment. To help you maintain this vigilance, we introduce the 'Be I AM' framework: Be Informed, Alert, and Mindful.
Be Informed
Stay abreast of the latest developments in cybersecurity. Threats evolve rapidly, and new vulnerabilities are discovered regularly. By keeping yourself informed, you can adapt your defense strategies accordingly. Follow reputable cybersecurity blogs, attend webinars, and consider obtaining certifications to deepen your knowledge.
Be Alert
Maintain a state of constant awareness regarding your digital presence. Regularly monitor your accounts for suspicious activity, keep an eye on your credit reports, and respond promptly to any security alerts. Remember, early detection is key to minimizing damage from cyber threats.
Be Mindful
Approach your online interactions with a security-first mindset. Before sharing information, posting on social media, or engaging in online transactions, pause to consider the potential security implications. Cultivate a habit of questioning the necessity and security of each digital action you take.
By embracing the 'Be I AM' framework, you transform cyber self-defense from a set of isolated actions into a holistic lifestyle approach. This mindset will serve you well as you navigate the ever-changing landscape of digital threats.
In conclusion, while the dark web and its associated threats may seem daunting, you are not powerless. By understanding the nature of these threats, implementing practical protection measures, utilizing monitoring tools, and maintaining a vigilant mindset, you can significantly reduce your vulnerability to cyber attacks.
Remember, in the digital age, your online identity is an extension of yourself. Protecting it is not just about safeguarding data; it's about preserving your personal and financial well-being. As we continue to integrate technology into every aspect of our lives, the importance of cyber self-defense will only grow. By taking action now and committing to ongoing vigilance, you are investing in a safer, more secure digital future for yourself.
The journey of cyber self-defense is continuous, but with the knowledge and strategies outlined in this guide, you are well-equipped to face the challenges that lie ahead. Stay informed, stay alert, stay mindful, and above all, stay safe in your digital endeavors.
Live Happily Ever Cyber!

Sandra Estok
Subscribe for more ways to protect what matters most to you against hackers, scammers, and Cybermonsters™



